Secure wiping of devices and media during their disposal processes is a standard security control that we recommend to our clients. There have been a number of examples of how failure to wipe hard drives prior to disposal has resulted in embarrassment to individuals or organisations.
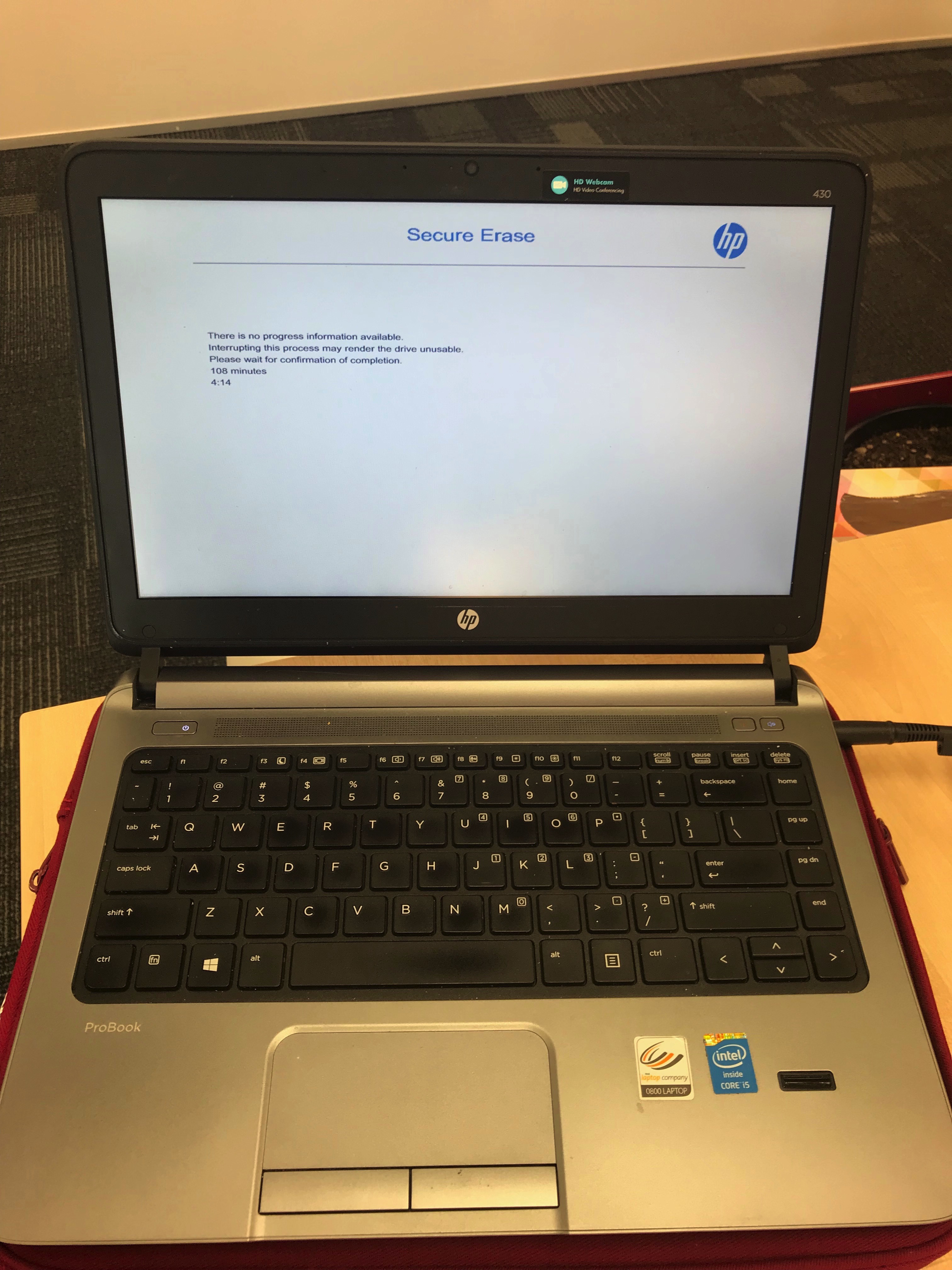
There is no shortage of research* highlighting the impact around data breaches when devices have been “disposed of”. As well as being common sense, it also meets the guidance/requirements of ISO 27001 (A.11.2.7) and the NZISM (13.6.7.C.01, 12.6.5.C.05).
What we do with unwanted Axenic devices
Over the last few years, we have accumulated a number of laptops that have reached the end of their practical working life for us or that no longer meet our standards (no TPM chip for example). They are still functional devices and should be able to be used in a less demanding environment. Axenic and its staff have supported the Karunai Illam children’s home in southern India for some time (see our 1 August blog) and one of our team suggested that they may be useful to the Illam. We confirmed with a local trustee of the trust that fundraises for the Illam that the laptops would be useful there. However before sending them we needed to be sure that no information that could be sensitive to our business or our clients remained on the devices.
This Monday we securely wiped the first two devices using our documented disposal process and they are now on their way to India for a new life.
We encourage everyone to recycle, reuse or re-purpose depreciated devices and media…just make sure that you securely wipe them first!
*If you are interesting in finding out more, this is a selection of the research and related articles around the importance of the secure disposal of your unwanted devices:
- Data breach concerns cause fear around device disposal
- Data destruction and its importance to secure your data privacy
- Analysis of information remaining on disks offered for sale on the second-hand market
- Zombie hard disks – Data from the living dead
- Missile data found on hard drives
- Discarded hard drives can be dangerous
We’d love to hear how you manage the safe disposal of your unwanted devices. Feel free to drop us a line here with your feedback and of course if you would like some advice from the information security experts at Axenic.